Privacy in Blockchain
Opening Quote
The original goal of using Blockchain, as per the Bitcoin whitepaper, was to anonymize financial transactions, as described below.
“The traditional banking model achieves a level of privacy by limiting access to information to the parties involved and the trusted third party. The necessity to announce all transactions publicly precludes this method, but privacy can still be maintained by breaking the flow of information in another place: by keeping public keys anonymous. The public can see that someone is sending an amount to someone else, but without information linking the transaction to anyone. This is similar to the level of information released by stock exchanges, where the time and size of individual trades, the “tape”, is made public, but without telling who the parties were.”
“The traditional banking model achieves a level of privacy by limiting access to information to the parties involved and the trusted third party. The necessity to announce all transactions publicly precludes this method, but privacy can still be maintained by breaking the flow of information in another place: by keeping public keys anonymous. The public can see that someone is sending an amount to someone else, but without information linking the transaction to anyone. This is similar to the level of information released by stock exchanges, where the time and size of individual trades, the “tape”, is made public, but without telling who the parties were.”
There is a lot of value in going back to read the original Bitcoin whitepaper here: it emphasizes the benefits of using Blockchain, as well as the requirements to gurauntee those benefits. We strongly recommend doing that before reading the rest of this content.
Privacy
Blockchain, and Cryptocurrency, have generally gained attention due to their strongly perceived anonymity. These guaruntees are largely created through the use of cryptography. It is pertinant to note that the cryptography in question that is commonly used is explained in the Bitcoin, and subsequent, whitepapers. It is important to understand that cryptography so some extent, to understand the shortcomings and superior methods for privacy.
There are many examples where individuals have been linked to their activity on Blockchain networks, however. For example, the earliest widely-adopted use case for Cryptocurrency was the Silk Road marketplace. On Silk Road, users could purchase anything, including illegal goods and services. This kicked off a large, illicit online community dealing in everything from drugs to hired crime. Ross Ulbricht, the founder of Silk Road, was arrested in 2013, 2 years after founding the website. He is now serving two life sentences.
Most users of Blockchain technology will not have to fear a lengthy FBI investigation into their identity. However, many individuals still hold on to the value of privacy in their financial lives. For example, an individual with large savings who wants to invest in Cryptocurrency may not want to paint a target on their back for hackers, kidnappers, or other criminals by having their identity linked to a Cryptocurrency wallet with millions of dollars. As a result, the Blockchain industry has sought systems that guaruntee privacy better than Bitcoin is able to.
Privacy Coins
Various systems have been developed to strengthen the guarantees offered by Blockchain and Cryptocurrency around privacy. Due to the governance and development models of most Blockchain projects, however, these innovations do not typically get implemented within existing projects. Instead, new projects spring up around them. These projects are known as "Privacy Coins"; most privacy coins today leverage zero-knowledge proofs or similar cryptology theory.
Privacy Coin: Cryptonote (Monero)
Monero is an open source Cryptocurrency based off the Cryptonote whitepaper written by Nicolas van Saberhagen. In the paper, van Saberhagen highlighs two key properties for a “fully anonymous electronic cash model”:
Suggested Readinglightbulb_outline
“Monero Research Lab”, including the Cryptonote Whitepaper that Monero is based on. van Saberhagen, 2013.Monero is an open source Cryptocurrency based off the Cryptonote whitepaper written by Nicolas van Saberhagen. In the paper, van Saberhagen highlighs two key properties for a “fully anonymous electronic cash model”:
Suggested Readinglightbulb_outline
“Monero Research Lab”, including the Cryptonote Whitepaper that Monero is based on. van Saberhagen, 2013.- Untraceability: for each incoming transaction, all possible senders are equiprobable.
- Unlinkability: for any two outgoing transactions, it is impossible to prove they were sent to the same person.
This point emphasizes the difference between the Cryptonote solution and Bitcoin: while Bitcoin has keys that are anonymous, it is fully possible to look through the fully public Blockchain of Bitcoin and find which transactions are going where, and who sent them. This means that once an identity is established for a transaction or wallet, it can be trivial work to trace that identity through their entire history on the Blockchain, unless that individual took special care to obfuscate links between wallets and transactions.
Nicolas van Saberhagen goes on to suggest zero knowledge proofs as a potential solution to this issue, comparing it and analyzing it from a Bitcoin reference point. I recommend reading the CryptoNote whitepaper for a thourough explanation of zero knowledge proofs, including ring transactions. This page may be updated in the future to include a summary of how zero knowledge proofs work.
Privacy Coin: Zcash
Zcash is another zero knowledge proof system privacy coin. It goes intro elaborate detail on implementing a relatively scalable Cryptocurrency while leveraging zero knowledge proofs. This does not necessarily mean that it is more scalable than Monero or other zero knowledge proof privacy coins, merely that the whitepaper goes more into detail analyzing the scalability of the proposed solution.”:
Suggested Readinglightbulb_outline
“Zerocash: Decentralized Anonymous Payments from Bitcoin (extended version)”, Sasson et al., 2014Zcash is another zero knowledge proof system privacy coin. It goes intro elaborate detail on implementing a relatively scalable Cryptocurrency while leveraging zero knowledge proofs. This does not necessarily mean that it is more scalable than Monero or other zero knowledge proof privacy coins, merely that the whitepaper goes more into detail analyzing the scalability of the proposed solution.”:
Suggested Readinglightbulb_outline
“Zerocash: Decentralized Anonymous Payments from Bitcoin (extended version)”, Sasson et al., 2014The following visualization will help with comparing the transparency of transactions on the public blockchain and bitcoin versus making use of zero knowledge proofs and something like Zcash.
This is a list of transactions as we would see on the public blockchain. It is easy to take a users address and find their real identity.
List of transactions
1F67WtwkgyV3 sent 1 BTC to 1DWod6wBBrRR
1F67WtwkgyV3 sent 5 BTC to 1EWsoa84RHBw
36RYGSB921qh sent 3 BTC to 1F67WtwkgyV3
36RYGSB921qh sent 1 BTC to 1DWod6wBBrRR
1DWod6wBBrRR sent 3 BTC to 14NeUdZT5RXV
Bitcoin transactions vs transactions using zero knowledge proofs
Privacy Coin: Enigma
Once the idea for Smart Contracts started to come up, most notably through Vitalik Buterin's Ethereum whitepaper, this dicussion of privacy began to expand beyond anonymity within financial transactions. Enigma is a project that looks to expand privacy into smart contracts.
The Enigma whitepaper outlines a system that can support smart contracts in a decentralized manner without exposing security vulnerabilities within the code, or the data being processed by the contracts. This expands the overall security and privacy for decentralized applications. These smart contracts are deemed 'secret contracts'.”:
Suggested Readinglightbulb_outline
“Enigma: Decentralized Computation Platform with Guaranteed Privacy”, Zyskind, Nathan, & Pentland, 2015 (MIT Media Lab)The Enigma whitepaper outlines a system that can support smart contracts in a decentralized manner without exposing security vulnerabilities within the code, or the data being processed by the contracts. This expands the overall security and privacy for decentralized applications. These smart contracts are deemed 'secret contracts'.”:
Suggested Readinglightbulb_outline
“Enigma: Decentralized Computation Platform with Guaranteed Privacy”, Zyskind, Nathan, & Pentland, 2015 (MIT Media Lab)
Enigma accomplishes secret contracts by creating a secure multi-party computation protocol as a second-layer solution. The whitepaper goes into detail on how they accomplished that, challenges they ran into, the incentives, punishments, and fees required to make the system work, and possible use cases of their solution (including: data marketplaces, secure backends, internal compartmentalization, N-Factor authentication, identity, IoT data, distributed personal data stores, crypto banks, e-voting, and Cryptocurrency wallets).
→
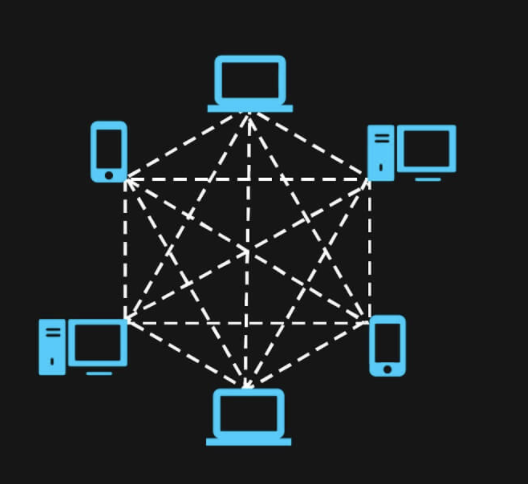
→
The difference between data served by the public blockchain vs Enigma
Possible Further Improvements
In general, most privacy coins leverage complex math, incentive economics, and cryptography. It is hard for either of us to predict which improvements will come up next, as neither of us specialize in cryptography. We anticipate that more secure privacy solution will arise around transactions and secret contracts, as well as Blockchain integration with the everyday internet.
Written By

James Gan @https://bellevue.tech
Software Engineer II at PayPal

Rishub Kumar @http://rishub.com
Solutions Engineer at Alchemyapi.io